Solutions
Your Trusted Partnerfor Cybersecurity needs.
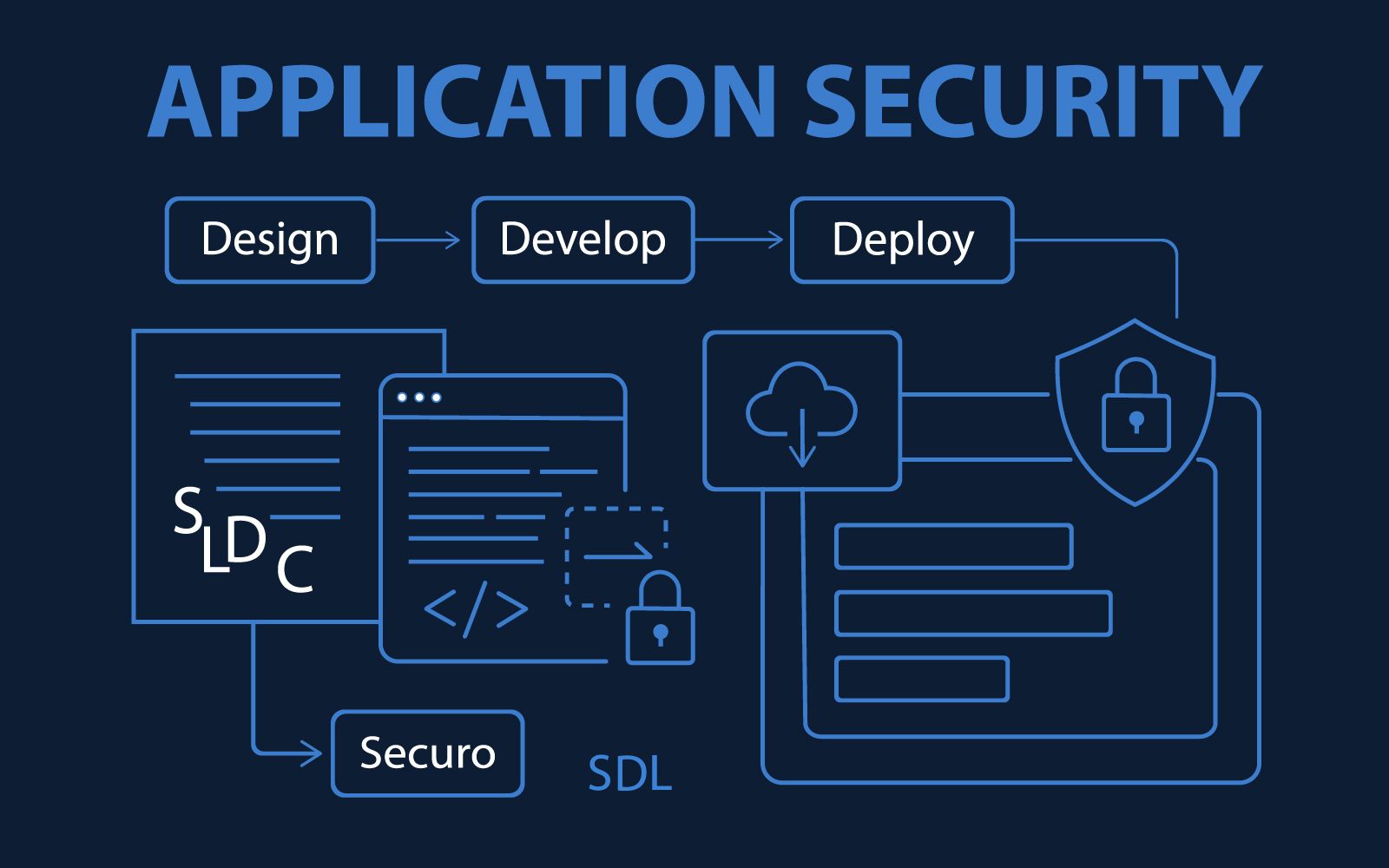
Application Security
Each aspect of a business is somehow dependent on applications – web applications, thick client applications and mobile applications. Attackers often target the software that controls information assets so they can steal data, hijack systems or disrupt operations.
WaveStrong provides secure development methods, a wide range of traditional application testing techniques and sophisticated security technology. We help our clients mitigate risks by identifying threats and implementing effective application security risk management programs.
- Web Application Firewall
- Web Application Testing
- Mobile Application Testing
- Client/Server Application Testing
- Secure Development and Methodology
- COTS Testing
AI Security
As organizations adopt AI and machine learning, they face unique risks like adversarial inputs, data poisoning, and model theft.
WaveStrong’s AI Security services help safeguard your AI/ML assets by securing training data and models, conducting AI-specific threat modeling, and implementing controls to protect algorithm integrity and confidentiality.
We address vulnerabilities across the AI lifecycle—from data ingestion to model deployment—ensuring that your AI systems are resilient against manipulation or leakage. With these measures, you can confidently leverage AI innovations while maintaining data privacy, compliance, and trust in AI-driven decisions.

Cloud Security
Moving to the cloud offers agility but also introduces new security challenges. WaveStrong’s Cloud Security services provide end-to-end protection for your cloud infrastructure, platforms, and applications.
We design secure cloud architectures and implement cloud-native controls (identity and access management, encryption, network segmentation, etc.) tailored to AWS, Azure, and Google Cloud environments.
Our team also deploys continuous monitoring and automated compliance checks to detect misconfigurations or threats in real time. By securing your public, private, and hybrid cloud deployments, we help you prevent data breaches, ensure compliance, and confidently embrace the benefits of cloud computing.
Data Protection
Data is the lifeblood of your organization, and protecting it at every stage is paramount. WaveStrong’s Data Protection services cover the full data lifecycle: we help you discover and classify sensitive data, enforce encryption and access controls, and deploy data loss prevention solutions.
Our experts can implement database activity monitoring (for example, using IBM Guardium for real-time auditing of database access) to detect and block suspicious behavior.
By establishing strong data governance and security controls, we ensure that your critical information remains confidential, intact, and compliant with regulations, from creation to deletion.


Cyber Center of Excellence
WaveStrong’s Cyber Center of Excellence (CCoE) is a dedicated team and knowledge hub focused on cybersecurity innovation and best practices. Through our CCoE, clients gain access to thought leadership, advanced research, and tailored frameworks to solve complex security challenges.
We collaborate with your organization to develop custom strategies, run workshops and training sessions, and pilot emerging security technologies in controlled environments.
By leveraging our CCoE, you accelerate your cybersecurity program’s maturity – benefiting from WaveStrong’s collective expertise and staying ahead of evolving threats with cutting-edge approaches.
Cyber Technology Rationalization
Enterprises often accumulate a patchwork of security tools over time, leading to inefficiencies and unnecessary costs. WaveStrong’s Cyber Technology Rationalization service evaluates your current security technology stack to identify overlapping tools, gaps, and opportunities for optimization.
We provide a strategic plan to consolidate and fine-tune your investments—selecting best-fit solutions, eliminating redundancies, and streamlining integrations. The result is a simplified, more effective security architecture that reduces complexity and operational overhead while maximizing the return on your cybersecurity investments.


Identity Transformation
In modern cybersecurity, identity is often considered the new perimeter that must be secured. WaveStrong’s Identity Transformation services help you evolve from legacy IAM systems to next-generation solutions that support Zero Trust principles.
We assess your current identity infrastructure and design improvements such as federated single sign-on, multi-factor authentication, identity governance automation, and privileged access management.
Our team guides you through implementing cloud-based identity platforms or hybrid models that enhance security and user experience. By transforming your IAM, we ensure only the right users get access to the right resources – reducing risk and enabling business agility.
Risk & Privacy
Organizations today must manage cybersecurity risk and privacy compliance side by side. WaveStrong helps you establish a unified governance, risk, and compliance (GRC) program that addresses both security risks and data privacy obligations.
We conduct enterprise risk assessments, develop risk treatment plans, and implement frameworks like NIST CSF or ISO 27001 to systematically reduce risk.
In parallel, we align your policies and controls with privacy regulations (GDPR, CCPA, etc.), ensuring proper data handling and breach response processes. By tackling risk and privacy in an integrated way, we help minimize the chance of costly incidents and penalties while bolstering customer trust.


Threat Detection and Response
Even with strong preventative measures, some attacks may still get through—prompt detection and response is critical to limit damage. WaveStrong’s Threat Detection and Response services enhance your ability to find and stop threats in real time.
We help deploy and fine-tune advanced monitoring solutions (SIEM, EDR, NDR) and integrate threat intelligence to spot suspicious activity early.
Our consultants also develop incident response plans and train your team in threat hunting and investigation techniques, so you can react swiftly and effectively to incidents. Through improved detection capabilities and practiced response, we significantly reduce attacker dwell time and strengthen your organization’s resilience to cyberattacks.